Often we hear some or the other major site being hacked or a sensitive database being compromised somewhere. It is scary to imagine that your website can be hacked or somebody can steal it from you.

If you remember about the recent Brute Force Attacks on WordPress websites, it was pretty bad. We had discussed about tightening the security of your website at the time in following post:
But one of the things that is not so critical as hacking of your website or a brute force attack is the challenge of comments spammers who can get you frustrated pretty quickly. In fact, it can be very frustrating for you and a lot more resource consuming process for your web server.
Since my website’s Alexa ranking came under 100000, I saw a sudden increase in the number of spam comments. Many times the CPU usage of my website was way above 150% of its entire capacity. It forced me to look for a robust remedy and I am going to share with you in this post as well.
Why Your WordPress Website’s Security Is Important
First things first. Staying vigilant about security of your WordPress website is an ongoing responsibility you must take.
It isn’t just for a WordPress website owner. Protecting your asset must be your responsibility and if your website is an asset to you, you must ensure its protection from various internet threats.
You might have heard that your website’s loading speed plays an important role in your search engine ranking. However, if your website gets infected with malware, speed can’t come to your rescue. Search engines will flag you down. Similarly, if you have a high ranked website and it gets hacked, you lose all the control of your website. Don’t worry, things I am going to share with you, are going to be easy to grasp and implement.
Although there is no 100% guarantee, here are some of the most important steps you can take to harden the security of your WordPress and protect your website from many commonly known internet threats:
1. Remove Default Admin Users
Do you have a user ‘admin’ or ‘administrator’ still active? Please note that WordPress installation creates one of these users by default. It is very natural that many webmasters do not remove this user from the system making it easier for hackers to guess the administrative user name for your website. All they have to do is to guess your password and they can get in.
You should create a custom user with administrative access to your website and remove ‘admin’ or ‘administrator’ accounts from your WordPress installation. Please note that it isn’t the pinnacle of security measures. But it makes your security, just a bit more tighter and I believe that every bit counts.
2. Make Your Passwords Hard To Guess
I hope you already have taken care of this aspect for your WordPress administrator accounts. If you haven’t, it’s time that you go ahead and make your passwords stronger and unique so it can’t be guessed.
When brute force attacks came, hackers try guessing passwords and if you have a password such as ‘password123’, ‘YourName123’ etc., you make yourself vulnerable.
3. Keep Your WordPress, Themes And Plugins Updated
WordPress comes up with updates frequently to fix bugs, introduce new features, or to patch security issues identified from time to time. Similarly, themes and plugins also get updated by their owners to cope up with the changes accordingly.
Therefore, it is important to keep your WordPress installation, themes and plugins updated with the new releases. Being at a current version of these components makes your WordPress less vulnerable to attacks. This is for your own good.
4. Implement Captcha Code For Login Screen
If you really want to make breaking into your website even harder, implementing a captcha code mechanism on your WordPress login screen as shown in the image below:
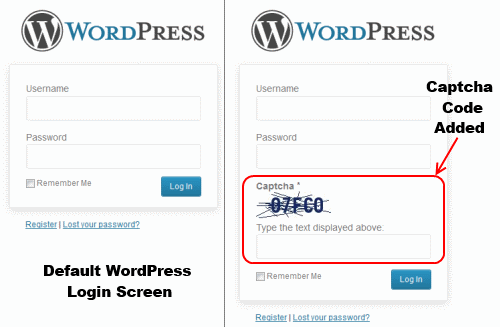
As you can see, it will be hard to automatically attempt to login using the scripted methods that hackers use when you have a captcha code implemented. You may use Captcha Code WordPress plugin for that purpose.
5. Limit Login Attempts To Your Website
The way brute force attacks on WordPress work is, hackers attempt to login using various username and password combinations over and over. The number of attempts a day could go in hundreds if not thousands consuming your resources and putting your website at risk.
There is a free WordPress plugin called Limit Login Attempts that will make it much more difficult for brute force techniques to work. It blocks an Internet address from making further attempts after a specified limit on retries is reached, making a brute-force attack difficult or impossible.
6. Use CloudFlare For Enhanced Security
I’ve implemented CloudFlare for a long time and I highly recommend that you implement CloudFlare on your website. It not only serves you as a free CDN but also helps you protect your WordPress installation to a great extent.
CloudFlare is a free content delivery network that filters all your traffic and minimizes the risk of your WordPress website from becoming a target. For more information about CloudFlare implementation, refer to this post.
7. Lock Down Your Server Using .htaccess Rules
The majority of the WordPress websites use the Apache HTTP server, a truly excellent, scalable and secure open-source web server. Chances are that your WordPress website is running on Apache as well. That means you have an effective built-in tool to fight spammers and hackers using an .htaccess file.
[note background=”#E4E4F2″]Disclaimer: .htaccess is a very powerful tool in your hand. Therefore,be extremely careful as you work on this file. You should take back up copies of this file before making any changes because mistakes can basically make your website totally inaccessible. I recommend that you seek professional help if you don’t know what you are doing when it comes to .htaccess file manipulation. [/note]
If you have W3 Total Cache installed, you should have a .htaccess file available in your HOME directory already. If you don’t have this file in your home directory, you can simply create a plain text file, make your entries and save it as “.htaccess”. Now, you can transfer this new .htaccess file using FTP to your website’s HOME directory.
The .htaccess rules I am going to share with you, should be entered in the beginning of your file in case you already have a file existing with existing .htaccess rules in it. Okay, let’s write some rules now.
8. Block Access To Sensitive Files
You don’t want everyone to read the content of your .htaccess file itself. Similarly, you shouldn’t allow people to see your other sensitive web server and WordPress files. Here is a quick code snippet to block access to these files:
[note background=”#E4E4F2″]<FilesMatch “\.(htaccess|htpasswd|ini|phps|fla|psd|log|sh)$”>
order allow,deny
deny from all
</FilesMatch>[/note]
In this code above, you are instructing the web server to deny access to the file requested if any file request contains .htaccess or .htpasswd or .ini or .phps or .fla or .psd or .log or .sh. If someone is tries to access any of these files, they will get a “403 – Forbidden” error message.
-
Ban Remote Access To Your WordPress Files (Login and Comments)
At one hand, hackers are trying to get access of your WordPress administration. On the other hand, “spamdexing” is attacking your website for spam link attempts. In spamdexing, spammers write scripts to leave fake comments on your blogs in an effort to boost the search engine rank for their own site.
In both the cases, you don’t want them to use your resources and block them from having any go in this case.
The code snippet given below will block any remote access to files in your wp-admin folder, wp-login.php and wp-comments-post.php file.
[note background=”#E4E4F2″]<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{REQUEST_URI} ^(.*)?wp-login.php(.*)$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-comments-post\.php*
RewriteCond %{HTTP_REFERER} !^http://www\.YourDomainName\.com [NC,OR]
RewriteCond %{HTTP_USER_AGENT} ^-?$
RewriteRule .* – [F,L]
</IfModule>[/note]
This .htaccess code snippet forbids the access to the files mentioned if somebody is trying to POST data through any of the files remotely.
Comment spammers were really troubling me before I implemented this rule. I used to get at least 15-20 spam comments (through remote access which causes comments to be posted without even entering the email address) each day.
But, since I have implemented this .htaccess rule, I have not received any spam comments in a few weeks now. I think this has saved me of a lot of heartache due to comment spammers.
-
Test Your .htaccess Entries To Ensure The Rules Work
Now, having made these entries, you want to make sure you are getting the results you expect with these new .htaccess rules that you’ve added. To do that, follow these steps:
- Go to http://www.botsvsbrowsers.com/SimulateUserAgent.asp
- You will be presented with a screen like the one shown below.
- Choose your request type as ‘POST’ and enter the URL as:
Now, as demonstrated in the image here, click on the ‘Send Request’ button.
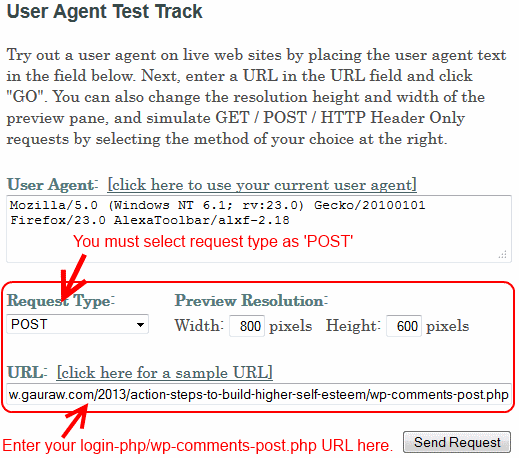
- It will prompt you to enter a CAPTCHA CODE. Enter the captcha and submit.
- If you see the status as “403-Forbidden”, then your .htaccess rules are working just as expected. Congratulations! You are all set.
- In case the status is coming as “200-OK”, then there must be a syntax error or a typo in the rule that is not letting the rule to work. Get professional help to get it fixed if you aren’t able to make it work by yourself.
Over To You…
Did I miss anything? Is there any other security measure that should be included in this post in addition to these? Please share your thoughts in the comments(scroll down or click here to go to comments). Thank you kindly!





This is an excellent post Kumar! What I enjoyed about your post is the last section. I found a way to test if my .htaccess rules work or not. Thanks for your wisdom.
Hi Gauraw !
You have mentioned excellent points on avoid brute force attacks .Apart from the above mentioned points , we should install a security plugin like wordfence which would automatically block an ip address that is trying to enter into our wp-admin dashboards .Anyways,thanks for sharing this information with us .
-Pramod
That is an excellent idea Pramod. Thanks for suggesting. However, If you have CloudFlare implemented, they do a great job as well.
Thank you so much for the info. Have to use captcha for
wordpress login. I used the plugin to limit login attempt to 4 to
add the security. Thanks for sharing nice tips bro.
Hello dear Kumar Gauraw. Thank you in advance for sharing this informative article with us. I think, using Akismet and a captcha plugin and limit login attempts can protect a WordPress blog properly. However, after reading your article properly this should more easing.
WordPress is certainly one of the most renown CMS out there on web. Almost anyone can create a website or personal blog using WordPress with little to none technical skill. But the major issue WordPress always has with is login vulnerability. If anyone is unable to hide log detail then his website might get compromised by a hacker. One must increase wordpress security to stay firm.
I’ve serious problem of comment spam on my blog, some friend recommended me Askimat plugin and I’ve installed it. But I’m not sure it’s working properly or not, is there anyway to check it’s working or not? Any help would be appreciated.